Understanding SOC-as-a-Service
SOC-as-a-Service, also known as Security Operations Center as a Service, is a solution that allows companies to outsource their cybersecurity operations to a specialized third-party service provider. This model is particularly beneficial for small and medium-sized enterprises (SMEs) that may not have the resources or the in-depth expertise to establish and maintain an in-house Security Operations Center (SOC).
One of the main drivers for organizations adopting SOC-as-a-Service is the increasing complexity and sophistication of cyber threats. Cybersecurity is not a static field - new vulnerabilities are discovered daily, attack methods evolve, and regulatory requirements tighten. Keeping pace with these changes requires an ongoing commitment of resources and specialized skills that many organizations struggle to maintain.
In the SOC-as-a-Service model, the service provider takes on the role of the SOC, using its own infrastructure, tools, and team of security experts to deliver the service. The client organization connects their IT infrastructure to the service provider's SOC through secure connections, allowing the provider to monitor the client's networks, servers, databases, and other IT assets for security incidents.
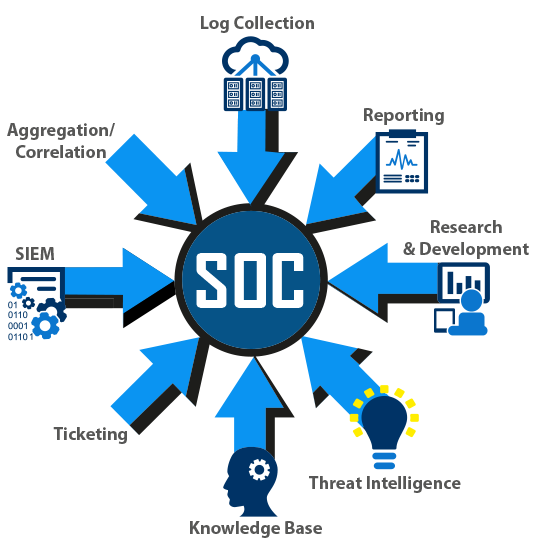
Key Features And Components Of A SOC
SOC-as-a-Service is a comprehensive cybersecurity solution that encompasses a variety of features and components, each designed to fortify an organization's defenses against potential cyber threats.
- 24/7 Monitoring and Incident Response: One of the foundational features of SOC-as-a-Service is its continuous, around-the-clock monitoring of an organization's digital infrastructure. As cyber threats don't operate on a traditional 9-5 schedule, it's crucial for organizations to have an unwavering vigilance towards their cybersecurity posture. Security incidents are promptly identified, analyzed, and responded to, either by the service provider's team directly or in close coordination with the client's internal IT team.
- Threat Intelligence: In the rapidly evolving landscape of cybersecurity, having real-time, actionable intelligence about emerging threats is paramount. SOC-as-a-Service providers leverage their broad visibility across multiple clients and industries to gather and analyze data on emerging threats and attack techniques. They use this threat intelligence to bolster their defensive capabilities and to provide proactive security measures for their clients.
- Compliance Assistance: For many organizations, especially those in heavily regulated industries, maintaining compliance with data security regulations is a significant challenge. SOC-as-a-Service providers can offer valuable assistance in this area, by aligning their services with the specific compliance requirements that a client faces. This can include providing necessary documentation and evidence for audits, and even acting as a liaison with regulators.
- Cloud-Based Infrastructure: The delivery of SOC-as-a-Service is primarily through a cloud-based infrastructure. This affords the service unparalleled scalability and flexibility, as organizations can easily adjust the level of service they receive based on their evolving needs. It also means that the service can be delivered anywhere, making it ideal for organizations with multiple locations or remote workers.
- Integrated Security Technologies: SOC-as-a-Service providers utilize a range of advanced security technologies to ensure comprehensive protection for their clients. These technologies are seamlessly integrated and managed by the provider, removing the burden of technology selection, integration, and management from the client. Technologies can include SIEM systems, IDS/IPS, endpoint detection and response (EDR), threat intelligence platforms, and more.
- Expert Personnel: One of the most valuable components of SOC-as-a-Service is the access it provides to a team of dedicated cybersecurity experts. These professionals bring with them a wealth of experience and knowledge, and are constantly updated with the latest cybersecurity trends and threat intelligence. They handle the day-to-day operations of the SOC, respond to incidents, generate and interpret security reports, and provide consultation to the client.
- Regular Reporting and Recommendations: SOC-as-a-Service providers regularly supply their clients with detailed reports that outline the status of their cybersecurity posture, provide an overview of detected threats and incidents, and offer recommendations for enhancing security. These reports are critical for strategic planning, demonstrating regulatory compliance, and fostering a better understanding of an organization's cybersecurity landscape.
Advantages Of Using A SOC As A Service (SOCaaS)
Advantages of SOC-as-a-Service:
- Cost Efficiency: One of the primary benefits of SOC-as-a-Service is the potential for cost savings. Unlike an in-house SOC, which requires significant upfront capital expenditure and ongoing operational costs, SOC-as-a-Service operates on a subscription basis, transforming those large capital expenditures into more manageable operating expenses. Moreover, it eliminates the need for organizations to invest in their own security infrastructure and maintain a full-time team of cybersecurity specialists.
- Access to Expertise: SOC-as-a-Service providers are cybersecurity specialists, with a team of experts who are well-versed in the latest threats, attack techniques, and defense strategies. These experts can offer a level of knowledge and experience that may be difficult for an organization to acquire and maintain in-house.
- Scalability: SOC-as-a-Service is a cloud-based solution, meaning it can easily scale with an organization's growth. As a company expands, its cybersecurity needs will grow as well, and SOC-as-a-Service can adapt to meet these changing needs without the need for substantial new investments.
- 24/7 Monitoring: Cyber threats don't keep business hours, which is why constant monitoring of an organization's IT environment is crucial. With SOC-as-a-Service, organizations benefit from around-the-clock surveillance of their digital assets, ensuring that potential security incidents are identified and addressed promptly, regardless of when they occur.